Infiltrator 3.0 - Network Security Scanning Software
![]()
Infiltrator is an easy to use, intuitive network security scanner that can quickly audit your network computers for vulnerabilities, exploits, and information enumerations. Infiltrator can reveal and catalog a plethora of information on scanned computers - such as installed software, shares, users, drives, hotfixes, NetBios and SNMP information, open ports and much more! Infiltrator can audit each computer's password and security policies, alerting you when changes should be made to increase security. All results can be generated into sleek, easy to read report by the report generator.
Infiltrator also comes with 18 powerful network utilities for footprinting, scanning, enumerating and gaining access to machines. Included utilities are ping sweep, whois lookups, email tracing, brute force cracking tools, share scanning, network enumerating, and many more.
Key Features
Information
Gathering |
Security Auditing and Analysis |
Generate Sleek Scan Reports |
Many Useful Network Utilities |
![]()
Infiltrator is powered by an extremely easy to use interface allowing quick access to all of its powerful and unique features. Read on to view Infiltrator's exciting features.
Information Gathering and Scanning
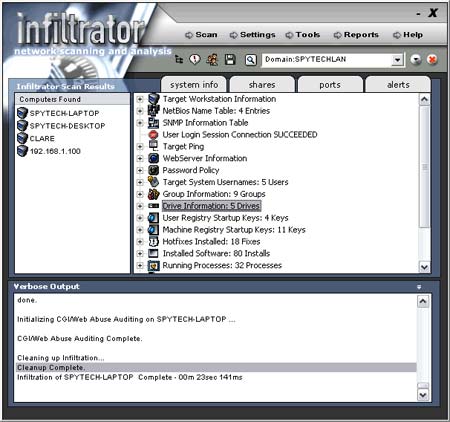
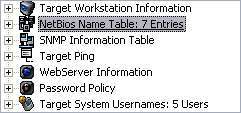
Infiltrator uses the very same scanning techniques that hackers and intruders would use to infiltrate your network and computers. In this fashion, you can see 'what a hacker sees' before they have a chance by scanning each computer on your network one IP at a time. Infiltrator scans target computers and attempts to enumerate as much information as possible. Infiltrator allows you to enter IP addresses, computer names, domains, website hosts, and IP ranges for easy scanning. Information that is enumerated includes, but is not limited to:
|
|
| Infiltrator in Action - Screenshots: | |
Security Auditing and Analysis
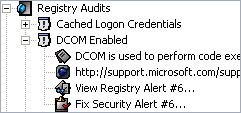
Infiltrator can audit each scanned computer and alert you of the following events using its own updatable, built-in auditing database:
|
| Infiltrator in Action - Screenshots: | |
Generate Sleek Scan Reports
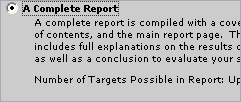
Infiltrator can generate brief or complete
reports based on your scan results. Brief reports allow for
scan results of one target, while complete results can encompass
an entire network's scan results into one organized, easy to
present and follow report. Complete reports include descriptions
and analysis of all results and conclude with evaluations of
each computer's security levels. Reports are fully customizable
(via html templates) and are easily presented in web or print
format.
| Infiltrator in Action - Screenshots: | |
Infiltrator comes with many built in network utilities, creating a robust suite of networking solutions suitable for any users. Utilities included:
Footprinting
Tools |
Scanning
Tools |
Enumeration
Tools |
Gaining
Access Tools |
| Infiltrator in Action - Screenshots: | |
User-Friendly,
Intuitive Interface
Infiltrator boasts a user interface unmatched by any other network security software. Infiltrator's easy to use, intuitive interface allows you to get started immediately with no having to 'learn the software'. Here are some key features of Infiltrator's powerful interface:
|
| Infiltrator in Action - Screenshots: | |
![]()
- Windows 2000, 2003, or Windows XP

- 3MB Hard disk space
- 128MB RAM
![]()
Price: $49.95
Instant Download!

Ordering is 100% safe via our authorized cleverbridge.com secure server.
 |
 |
![]()
Main Page: Internet Monitoring Software |
Copyright (C) 2002 - 2022 How To Spy Internet Monitoring Software - All Rights Reserved